Gunfight at OK Corral: MPLS vs. Probing


Benoit Donnet
Based in Université de Liège
Prof. Dr. Benoit Donnet is Associate Professor in the EECS department of the University of Liège. He received his Ph.D. degree in computer science from the Université Pierre et Marie Curie in 2006. He has published about 70 papers in peer-reviewed journals and conferences. His research interests are in Internet … More
• 10 min read
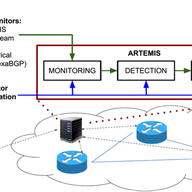
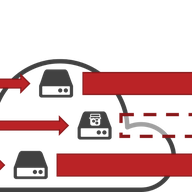
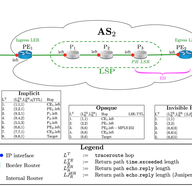
In this article, we investigate the various relationships between MPLS tunnels and standard probing techniques (i.e., ping and traceroute). We investigate several possible MPLS configurations and explain how they interact with measurement techniques. We also provide an external link to an online…