Timeline for Phasing Out the Old TTM-based DNSMON


Romeo Zwart
Based in Amsterdam (NL)
Former manager of the Global Information Infrastructure team at the RIPE NCC. More
• 3 min read
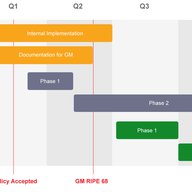
The RIPE NCC announced a new version of DNSMON, available for testing by the public, in March 2014. We are now planning the removal of the old DNSMON.