Choice of communication tools is not usually a topic for RIPE community engineers. This article is aimed at not-so-technical audiences who might need help and support from their IT colleagues during these difficult times.
Questions & comments are welcome! If you have questions or remarks, please add your comments below. We will be keeping this article updated on demand.
Today, people are actively looking for safe and secure communication, while preserving privacy, with their family, friends, and colleagues within and between countries in conflict. This article provides some concrete guidelines to those who need to communicate at some level of security. These guidelines are not about finding a perfectly secure solution but about practical, immediate possible actions with respect to email, instant messaging, voice and video chats, and other important security measures to consider.
The Internet architecture and technologies could allow for a perfect solution. But, as usual, the world is not perfect. This is the reason why we focus on solutions that provide a trade-off between secure and immediate-to-use solutions.
Assume the following concrete scenario: You are an organisation that has a branch office in a country in crisis. You need to communicate with your colleagues to coordinate your shared work.
Which email provider, messenger, or audio/video solution should you use, without being afraid of wiretapping? At the end, the answer is simple: Whom do you trust?
Remember two important things:
- There is no perfect technical solution, so do not believe that this or that software will give you complete safety. In some countries or situations, there is always a risk. Good software can mitigate it, not suppress it.
- In some countries or situations, using precautions such as an "unusual" software can be precisely the thing that will draw unwanted attention to you. In the end, it depends on the specifics of your situation and your country.
Setting the stage
When you send data via the Internet, others may read it. To prevent further harm, data should be encrypted. There are basically two options. First, an encrypted communication channel between two end points in the Internet. Second, encrypting the data before the data is sent via the Internet. The second option has the advantage that security of data is independent of the capabilities of intermediaries. On the other hand, it is harder to achieve because of key management for the encryption/decryption process. This is the reason why data is often not encrypted by the original data source (e.g., the email that you write and send) but only on the channels between intermediaries. Unfortunately, an end user has no influence on the security properties of communication channels that the user is not directly connected to.
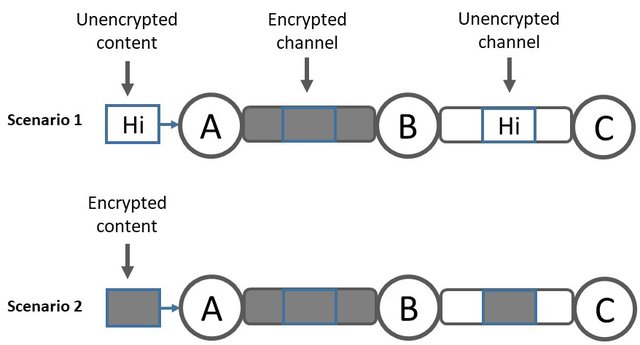
When you exchange emails, ensure that your email application uses an encrypted channel (e.g., SSL, TLS) between your application and your email server. All decent email providers support this level of security.
Preferably, you and your communication parties are also able to encrypt your emails completely by using S/MIME or OpenPGP, or attaching an encrypted file. Most likely, content instead of channel encryption is not (easily) possible, though. Then, it is recommended that you and your communication parties use the same email provider (i.e., have an email address under @gmail.com, @gmx.net, @<your choice>). Using the same email provider reduces the chance that your email will be delivered unencrypted over the Internet.
To allow for redundancy in case one of the email providers is not reachable anymore, you can create accounts at multiple providers.
If you have multiple email accounts at different email providers, verify that your email is not forwarded from one account to another, otherwise, it may be delivered via an insecure communication channel.
If you use different email providers between parties, try to check that your email provider uses encryption (SMTP over TLS) to protect its communications with other email providers.
An example of a secure email provider is ProtonMail. This Swiss based company offers a free, end-to-end encrypted, email service.
Instant Messaging
There are a plethora of instant messenger systems available, providing very different properties. One of the important criteria is that the messages are encrypted end-to-end.
If you have a service that you trust, use it! But keep in mind that a service that has a relation to conflict zone might be less reliable or less secure.
How can you know that a messenger is secure? Here are the assessments of messaging applications by several neutral organisations
Three messaging apps that scored highest, for beginners, on all three rating sites are:
- Session https://getsession.org
- Threema, https://threema.ch/
- Signal, https://signal.org/
Complementary security is achieved through the messaging system being decentralised, rather than operated from one central point (that can be taken over, surveyed or tampered with).
Concerning a decentralised system, https://element.io/ and https://newnode.com/ are advised. Element is based on matrix, an open messaging protocol that relies on common Internet standards.
Several people are also using Delta Chat (https://delta.chat/) as an alternative to Signal because Delta Chat does not rely on phone numbers (which can be tracked) and is e2ee based on open source libraries.
Voice and Video Chats
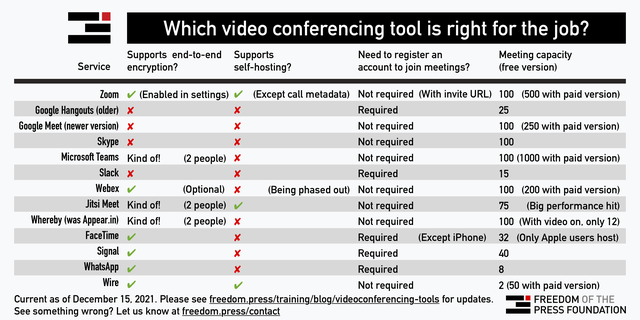
If you have a service that you trust, use it! Most of the free and commercial conference applications allow the encryption of audio and video streams (e.g., Skype, Zoom, WebEx, Jitsi) and they apply it by default. Just check the web page of your trusted app.
If you do not trust a central service provider, you may want to use https://element.io/ or https://wire.com/en/.
Anonymous Communication and Circumventing Censorship
The administration of the conflict zone may start to limit Internet access by different measures.
You can bypass a set of filters and enable anonymous communication by using overlay networks such as Tor. Those networks run on top of the Internet, encapsulate Internet traffic, and let look it differently.
Some popular websites provide their content via Tor. If you want to access the Web content via Tor, you need a Tor-enabled browser (e.g., Tor Browser) and you need to know the Tor URL (e.g., https://www.bbcnewsd73hkzno2ini43t4gblxvycyac5aw4gnv7t2rccijh7745uqd.onion/ instead of https://www.bbc.com/).
Here is a list of some popular websites that mirror their content to the Tor network -- whether these services will be available in the long term remains unclear:
A typical way of tracking and filtering inside the conflict zone is observing and manipulating the Domain Name System (DNS), the system that maps names to Internet addresses. Use a reputable DNS resolver with DNSSEC validation, and encrypted communication between your client and the DNS server (e.g., DNS over HTTPS). One example of a reputable DNS service is 9.9.9.9 (IPv4) and 2620:fe::fe (IPv6), details https://www.quad9.net/.
Your Local PC
If you are afraid that your on-site computer gets confiscated, store your data on a removal storage, e.g., USB key, which you detach on time. If you store data somewhere in the cloud, be aware that many cloud clients cache data locally. Additionally, you can cipher your hard disk or USB key using tools such as https://veracrypt.fr/en/, but note it may affect the performance of your PC and, most importantly, you need to remember the password otherwise your data will be lost.
Apple macOS (FileVault) and Microsoft Windows (Device Encryption, Bitlocker, EFS) both have integrated options to encrypt the data on your hard drive. It is easy to switch on, but you will have to trust these vendors to have done a good job.
Other Important Security Measures To Consider
An essential measure to protect your data is to avoid account compromise (especially for 3rd party services such as Gmail or ProtonMail) by enabling Multi-Factor Authentication (MFA). MFA combines multiple independent secrets. The most basic form of Multi-Factor Authentication is Two-Factor Authentication (2FA), e.g., a static password and a dynamically generated code sent to your mobile. This way, if your password is ever leaked or compromised, attackers will not be able to gain access to your account(s) and your data.
Further options to protect accounts include using strong passwords and not reusing them. This can be facilitated by using a password manager. Although the variety of options can be overwhelming, the main choice comes down to 'local or cloud'. Local password manages like KeePass provide the highest level of security but have significant usage downsides. Cloud-based password managers like Keeper however offer multi-device synchronisation, automated account breach checks, and some can even attempt to automatically reset passwords for accounts periodically.
The best way to avoid compromise (and protect your data) is to install all software updates, security updates, and OS updates. You should enable 'auto update' options were possible (e.g., sufficient bandwidth, high availability of connectivity). This is important for computers and mobile devices alike.
And do not forget ... whom do you trust?
- There is no perfect technical solution, so do not believe that this or that software will give you complete safety. In some countries or situations, there is always a risk. Good software can mitigate it, not suppress it.
- In some countries or situations, using precautions such as an "unusual" software can be precisely the thing that will draw unwanted attention to you. In the end, it depends on the specifics of your situation and your country.
Additional Sources
- Tools for Communicating Offline and in Difficult Circumstances [complete.org]
- Digital Security Assessment and List of Localized Tools [localizationlab.org/]
- Here's how to share sensitive leaks with the press [freedom.press]
- Surveillance Self-Defense Tips, Tools and How-Tos for Safer Online Communications [ssd.eff.org]
- Choose Privacy: Tools and Extensions for Securing Your Personal Data [medium.com]
Acknowledgments
We would like to thank all who gave feedback on a preliminary version of this post.


Comments 3
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Theodor Avram •
Hi Matthias. A couple of points which I think would be quite important to include when dealing with TOR is that the TOR network is definitely not enough to ensure browser traffic privacy against a strong state actor. TOR should be used along with a VPN in either a TOR-over-VPN or VPN-over-TOR and people should switch between them depending if they are using an .onion domain or not. These configs are fairly easy to apply nowadays so they should suit a novice user well. Here's an article detailing what I am referring to: https://securethoughts.com/vulnerable-use-tor/
Randy Bush •
nice piece. thanks. a few things: - personally, i much prefer signal - i use pgp email, but it sends a big signal that you may be doing something subversive - if you need to have a secure conversation with a friend, do not use electronic media. whisper in their ear in a noisy, moving, and crowded metro car.
xxm •
xx Messenger is decentralized, E2E encrypted and doesn't require a phone number. Available for iOS and Android (open source). https://xx.network/messenger/