Over the past months, SIDN Labs have been improving the testbed they developed for the DDoS Clearing House. At the CONCORDIA Open Door event (COD2022) this October, they'll demonstrate how the testbed works as part of the CONCORDIA Threat Intelligence Platform. The team look at the latest changes to the testbed and plans for COD2022.
In one of our previous posts over on the SIDN Labs blog, we introduced the testbed we developed for the DDoS Clearing House and described how we used it to pilot the system in a realistic environment. In this post, we want to bring you up to date on the latest changes to the testbed and our plans for COD2022 and invite you to visit our booth to see the platform in action.
DDoS Clearing House
The DDoS Clearing House is a system that enables organisations to share measurements of the DDoS attacks they handle in the form of so-called “DDoS fingerprints”. The Clearing House widens these organisations' view of the DDoS attack landscape, enabling them to prepare their networks for such attacks or make better decisions as to what third-party mitigation services to purchase. The DDoS Clearing House is an additional layer of security that complements DDoS mitigation services, which organisations need to have in place to handle actual DDoS traffic.
Anti-DDoS Coalitions
An Anti-DDoS Coalition (ADC) is a group of organisations committed to the common goal of improving the resilience of the services that group members offer to their users, by fighting DDoS attacks on a cooperative basis. The members of an ADC pursue that common goal through three types of activity: sharing DDoS fingerprints through the ADC’s DDoS Clearing House, collaboratively carrying out large-scale DDoS drills to test members’ DDoS readiness, and sharing DDoS expertise.
A testbed for the DDoS Clearing House
Last year, we set up a testbed to test the DDoS Clearing House in a simulated environment that is representative of a production scenario (see video). The testbed allows us to experiment with new versions of the Clearing House components, avoiding having to meddle in operational systems of existing anti-DDoS coalition members, and avoiding the cost of setting up data sharing agreements for exchanging real DDoS information. (Of course, such agreements do need to be in place for the production version.)
In short, the testbed consists of a traffic generator, capable of sending simulated DDoS traffic to a test network, and a virtual anti-DDoS coalition, connecting participating CONCORDIA partners. The traffic simulator is made up of five virtual machines distributed throughout the world, to resemble a botnet. An online dashboard enables easy interaction with the traffic generator.
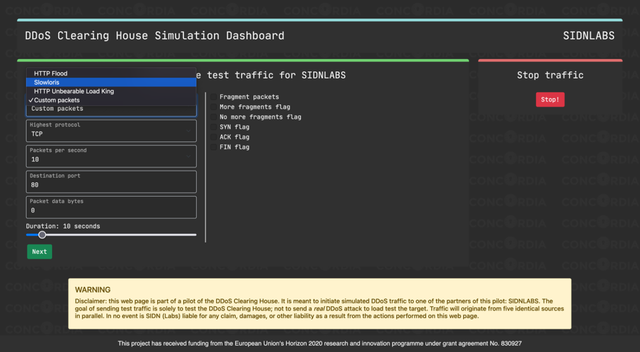
Our updated testbed: better, faster, stronger
In the past months, we have updated the testbed in two aspects. First, we improved its automation using Ansible, a popular automation language. With Ansible, the virtual machines that make up the “botnet” of the traffic generator can be managed with simple configuration files, ensuring every virtual machine is set up the same way. It also improves the way instructions are sent from the dashboard to the pseudo-botnet.
Second, we have introduced more attack types to the testbed. Previously, the testbed used hping3 to generate roughly identical packets and send them to the target in a steady stream, restricting it to Layer 3 and Layer 4 attacks. By integrating popular open-source DDoS testing tools into the testbed, we can now also test the DDoS Clearing House with different kinds of (layer 7) DDoS attack types.
We incorporated the following DDoS tools:
- HTTP Unbearable Load King (HULK): attempts to overload the target with many concurrent HTTP GET or POST requests, using random User Agent headers.
- Goldeneye: exploits the HTTP Keep Alive and No Cache attack vectors to quickly occupy a target’s resources.
- Slowloris: creates many HTTP requests and sends headers periodically to keep the connections open. By never closing the connections it exhausts the target’s thread pool, rendering it unable to respond to legitimate users. It uses very little bandwidth.
We remain on the lookout for more DDoS tools to add to the testbed to keep improving its versatility. The user interface remains practically the same, with an extra option to select the attack type and some visual changes (see Figure 1).
CONCORDIA Threat Intelligence Platform
The DDoS Clearing House is part of the CONCORDIA Threat Intelligence Platform, together with the Incident Clearing House and MISP. The platform supports informed cybersecurity decision-making by connected organisations, by providing information about attack techniques, indicators of compromises, and vulnerabilities. The process is collaborative in that all organisations on the platform contribute insights and data, and it is based on real-world datasets.
Threat Intelligence Platform demonstrator
We have developed a demonstrator that showcases the new platform in a cooperative and interactive demonstration. The demo shows three components of the Threat Intelligence Platform working together (the updated DDoS Clearing House testbed, MISP, and the Incident Clearing House) and walks through the hypothetical scenario shown in Figure 2.
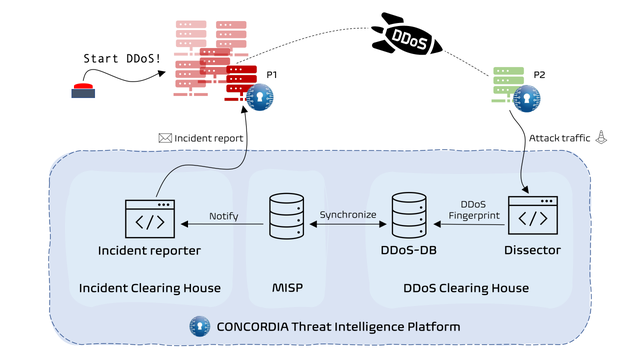
In the scenario, the CONCORDIA Threat Intelligence Platform is used by two partners, drawn in Figure 2 as servers P1 and P2. P1 is infected with malware and is now part of a botnet, capable of sending various DDoS attacks.
Using the botnet, the attacker starts a DDoS attack on the unsuspecting second partner, P2. The target collects traffic samples of the incoming DDoS attack for use by the DDoS Clearing House. The Dissector component uses the DDoS traffic samples to generate a DDoS fingerprint summarising the attack. It then automatically uploads the fingerprint to the DDoS-DB, which enables other members of the virtual ADC to obtain the fingerprint as well.
At the same time, a central MISP instance synchronises with the DDoS-DB to receive the newly uploaded fingerprint and stores it as a DDoS event. The Incident Clearing House uses the newly created DDoS event in MISP to enrich the incident report and send it to the compromised partner (P1), which is one of the sources of the attack. The Incident Clearing House can then also update the sightings of the incident in MISP.
CONCORDIA Open Door
We will present our interactive demonstration of the DDoS Clearing House at the CONCORDIA Open Door event (COD2022) and exhibit how our work can interact with the CONCORDIA Threat Intelligence platform. Other CONCORDIANs will also showcase the results they obtained over the past year at COD2022 to both project partners and other interested stakeholders. CONCORDIA ends at the end of this year and so this will be the last edition of COD. It takes place on 26 and 27 October in Munich, Germany.
That’s where you come in!

Did we mention the demo is live and interactive? We're therefore inviting you to join us at the demo stand in Munich, where you'll be able to use the DDoS testbed to craft a DDoS attack and push the Big Red Button to launch it. Because you will be kicking off the chain of actions described above, you will receive a copy of the incident report; better not let Interpol find out!
You can find more information about the CONCORDIA Open Door event here. If you are interested in more information about the DDoS Clearing House, anti-DDoS coalitions, or the Incident Clearing House, see the additional resources linked below or simply drop us an e-mail.
Read more
DDoS Clearing House source code: https://github.com/ddos-clearing-house
Blogposts:
Acknowledgements
This work was partly funded by the European Union’s Horizon 2020 Research and Innovation programme under Grant Agreement No 830927. Project website: https://www.concordia-h2020.eu/.
This article was originally published over on the SIDN Labs blog.



Comments 0
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.