RIPE 89 is the fourth time that a RIPE Meeting is being held in beautiful Prague, resplendent in its autumnal colours. You can view the slides, you can watch the recordings, but if you're wondering what's really happening at RIPE 89, read the daily meeting blog!
Day Five: BGP Zombies
After a spooky Halloween evening, the last day of RIPE 89 began very reasonably with a long coffee break. Then, we dove right into our first plenary of the day, where Henry Birge-Lee of Princeton University taught us about global BGP attacks that had the ability to hide themselves from BGP monitoring systems. Henry’s presentation offered guidance and countermeasures to providers to protect themselves against such attacks. A series of lighting talks then followed from Jen Linkova, Marcel Koch and Iliana Xygkou. Jen presented on the recommendation from the IETF that operators and implementors stop using RFC7050 (DNS64-based) NAT64 prefix discovery (resolving ‘ipv4only.arpa’) in favour of more reliable methods. Marcel gave an update on the efforts to build the IXP DD-IX. Finally, Iliana presented on the Global Routing Intelligence Platform (GRIP), which was developed to track BGP routing incidents.
Then, it was time for the Closing Plenary. Antonios Chariton and Iliana Xygkou of Cisco presented their study about the problems of stuck routes, also known as BGP zombies (a good Halloween costume idea for next year!). Lots of people filled up the microphone queues to ask questions. Then, Franziska Lichtblau gave a report from the RIPE Code of Conduct Team. She shared that there had been two cases during RIPE 88 that the team had been working on, but none so far at RIPE 89. And we learned that Vesna Manojlovic will be leaving the team. Thanks to Vesna for her contributions, from starting off as a Trusted Contact at RIPE 77 to joining the CoC Team!
Next, Rob de Meester of the RIPE NCC gave the RIPE 89 Tech Report. We learned that much has changed since the last RIPE Meeting in Prague, RIPE 60 - there was only about 6% IPv6 traffic then. Now the main network was mostly IPv6.
Rob also shared some challenges the team had faced, such as flight cases full of critical equipment dropped on the ground by the bus driver. He also addressed the problems with pre-recorded videos that happened during the May General Meeting, which kept Rob awake at night but have now been fixed. Live and learn! The report also showed that the access points at the hotel bar measured the highest number of clients during the Welcome Reception, and this meeting counted the highest number of espresso shots per day. Rob was proud to announce that one complaint at RIPE 88 had been taken care of—the connectivity in the toilets, of course!
RIPE Chair Mirjam Kühne concluded the meeting. She shared statistics on attendance at the meeting and the RIPE 89 local hubs. She also announced that Andrei Robachevsky was elected to the NRO NC, and she congratulated the newly elected RIPE Programme Committee members Antonio Prado and Babak Farrokhi and newly selected RIPE Working Group Chairs Stefan Wahl in RIPE NCC Services, Achilleas Kemos and Julf Helsingius in Cooperation, Marco d'Itri in Open Source and Sebastian Becker in Routing. She thanked the host and sponsors, and the RIPE NCC meeting team for their work. Finally, Eugénio Pinto of Associação DNS.PT came to the stage to invite attendees to RIPE 90, which will take place in Lisbon, Portugal on 12-16 May 2025.
We learned from our local host representative Ondřej Filip this week that Czech people have an interest in non-existent things. And speaking of non-existent things, we most certainly did not hear next from a working group that most certainly does not exist at the end of this plenary…
And with that, this RIPE Meeting concluded. We had a fabulous time here in Prague, and we’re grateful to everyone who contributed to #RIPE89! Now we’re already looking forward to a sunny #RIPE90 in Lisbon. We hope we’ll see you there!
Day 4: Trick...or treat?
Day 4 was lit up with the festive light of Diwali and spooks of Halloween. From illuminating technical talks to eerily insightful panel discussions, it’s been a day full of treats (and maybe a few tricks) in Prague.
IPv6 WG
The IPv6 Working Group began with a scary question from Geoff Huston; ‘Why Is This IPv6 Transition Taking So long?’. Despite IPv4 running dry over a decade ago, he said IPv6 uptake remains sluggish, largely thanks to NATs and the unexpected abundance of resources shifting priorities. IPv4 is hanging on and “the plan” went off the rails.
Next up, Nico Schottelius presented remotely on IPv6 in Kubernetes. He dove into the wild world of deploying routers with Kubernetes. It’s a tale of balancing k8s's app-centric mindset with the stubborn demands of networking. Using Kubernetes for router deployment offers structure and reproducibility, but it's not always smooth sailing: think image download dilemmas, single-node cluster setups, and GitOps roller coasters. The message? Routing can be done in k8s—but brace for a bumpy, containerised ride!
It might be Halloween but it’s never too early to talk about Christmas, is it? Jens Link shared his “Advent of IPv6” advent calendar idea to separate true IPv6 pros from the pretenders. Inspired by interactive coding and cybersecurity events, the idea involves a series of tasks with potential prizes and sponsor support, the challenge aims to be both fun and a real skills test.
Benedikt Stockebrand’s “Where are we with IPv6?” took a no-nonsense look at IPv6 progress. While we’ve “saved the Internet”, issues like transition tech and fragmented connectivity persist. The future holds a divided Internet and growing routing tables, so now’s the time to educate clients, keep an eye on BGP tables, and enforce RPKI. And no, there were no silly cats—just solid IPv6 advice!
Connect WG
It was Stavros and Paul’s first time chairing the session since being elected, they introduced Leo Vegoda who provided a PeeringDB update and Barry O'Donovan from INEX introduced the IXP Manager v7.
Max Stucchi dove into Italy’s Internet censorship saga, where a new anti-piracy law turned into a digital disaster. A heavy-handed anti-piracy law passed in July 2023 has caused digital mayhem. ISPs have just 30 minutes to block offending domains, leading to accidental disruptions of major services like Cloudflare and Google Drive. Unblocking can take hours, transparency is nonexistent, and compliance pressure is mounting, with ISPs facing jail time for failures. The blocklist now includes nearly 17,000 domains and 6,000 IP addresses (no IPv6 yet). Ironically, this law was supposed to save money and add jobs, but it’s mainly generating backlash. And with the new law on the horizon, the saga is getting a new chapter rather than an ending.

In a lively panel discussion moderated by Paul Hoogsteder, industry pros gathered to chat about the ever-evolving world of Internet exchanges (IXPs). With exchanges now boasting thousands of members, the days of picking up the phone to resolve issues are long gone! Panellists Tom Strickx from Cloudflare and Theo Voss from Inter.link shared their experiences being on the receiving end of the IXP communication, noting the hit-or-miss nature of outage notifications—sometimes too much info, sometimes not enough. They suggested clearer communication and better automation to keep everyone in the loop.
The clear takeaway from the following discussion: do not subscribe to the mailing list with your ticketing system and please, please, please do not abuse that reply-all button!
Database WG
At the Database Working Group session, Edward Shryane, RIPE NCC updated the community about discontinuing MD5 Hashed Passwords and transition to API Keys and asked the audience if UTF-8 should be supported in the RIPE Database.
Naturally the longest queue at the microphone gathered after the talk “Dead-ends and Car Parks” from Lee Kent, beIN. Lee was looking to engage with the RIPE community on inaccurate contact information in the RIPE Database and made a few suggestions on which processes could help to resolve disputes.
Open Source WG
The Open Source Working Group conjured up some updates including the announcement of Marco d’Itri as new Co-Chair who will be replacing Martin Winter, who is stepping down at this meeting.
Barry O’Donovan then took the stage to explain how the team at INEX uses Vagrant to automagically spin up fully functional development environments to enable quick dev iterations on IXP-Manager. This approach allows developers with little sys- or net- admin experience to work on visualisations and interfaces to a full set of BGP daemons, looking glass and SNMP simulators.
Pascal Gloor introduced Piranha, a powerful set of BGP debugging tools and demonstrated how it can help make sense of route data. August Bourrique picked up where he left off on Monday with his lightning talk on the EU’s Cyber Resilience Act (CRA), zooming in on its implications for Free/Open Source Software.
Vesna Manojlovic kept the momentum going by inviting everyone to join the Green Tech Hackathon in December, either online or in Amsterdam, to brainstorm sustainable tech solutions. Maria Matejka proposed a promising new tool for transforming data between CBOR/JSON and YANG, and she welcomed input as development kicks off.
The session wrapped up with heartfelt thanks to Martin Winter for over 11 years of dedication, celebrating with apple wine, Spanish whisky (yes, really), and stroopwafels.
Cooperation WG
Demonstrating the spirit of cooperation, Achilleas and Julf were reselected as Working Group Chairs without opposition and the first session featured a panel on WSIS+20. They urged members of the technical community to get involved, form alliances, and actively contribute. As Nigel Hickson put it, “It’s always good to talk to friends…well, I don’t have many…but talk to everyone!” Panellists also talked about the need for different national governments and governmental bodies to align in these processes (easy, right?).
Chris Buckridge presented a study commissioned by CIRA on the achievements of WSIS and sought the technical community's insights on challenges and solutions in the multistakeholder model. Hisham Ibrahim outlined RIPE NCC's governmental outreach efforts, including a proposed “front-door” process. Finally, Jim Reid gave an update from the ITU World Telecommunications Standard Assembly, where the only notable change was Resolution 64, reaffirming the key role of RIRs in IP address allocation (a sentiment we can all support!).
Routing WG
Johann Schlamp kicked things off with "Agree to Disagree," a dive into the inconsistencies of BGP parsing that left us pondering the quirks of BGP/MRT. Tim Bruijnzeels then gave the "RIPE RPKI Update," featuring shiny new releases like the RPKI Dashboard and the SOC 2 Type Assurance report, and took us through the RPKI signing process. Petros Gigis followed with "Bad Packets Come Back, Worse Ones Don’t," showcasing Penny, a nifty tool to sniff out spoofed traffic. The session wrapped with the Routing WG chair election: after a suspenseful round of jokes as we waited for the Meetecho poll, Sebastian Becker was named Co-Chair. Congrats, Sebastian!
RIPE Community Plenary - QR-ated Talks
It’s not all Halloween today - RIPE Chair Mirjam Kühne wished everyone a happy Diwali, the festival of light. The RIPE community plenary had a packed agenda with the NCC’s own Fergal Cunningham talking about the challenges of translation and Pedro Vaz marking 10 years of the RIPE NCC Academy (happy birthday Academy!).

IANA’s Kim Davies spoke about the upcoming root zone KSK rollover, followed by a discussion on post-quantum cryptography-based algorithms. He invited the audience to fill in a survey, sharing the QR code. Hervé Clément spoke about the ICP-2 revision process and shared a QR-code to fill it in. Jan Žorž also invited volunteers for the NomCom, and shared a link to a form, but he clearly missed the memo to have a QR code… There was an update from the RIPE Code of Conduct team and a discussion on the new media accreditation policy. If any journalists are reading this blog, make note that the CoC applies to you!
BoF, BoF
The day came to an end with not one, but two BoFs. Ideas flew around the DNS Resolver Recommendations in Practice BoF where a panel sized up how current resolver operations stack up against the guidance from ripe-823.
Meanwhile, over in the side room, getting off to a lively start, a panel-discussion-style BoF for NOGs led by the RIPE NCC's very dapper Alastair Strachan. Six NOG organisers on the stage and many more in the room discussed growing pains, logistics, the importance of bringing younger people to the network, varied challenges for NOGs across countries, and much more on the present and future state of NOGs.

Day 3: It's WGs All The Way Down
Day three was a jam-packed day full of working group sessions. How many flavours of IP address should we have in the RIPE Database - read on to find out!
Address Policy WG I
The Address Policy WG session opened with condolences for Erik Bais, who sadly passed away shortly after RIPE 88. Alex le Heux and others in the room shared many touching words about Erik before a moment of silence was held in his memory. Then, honouring Erik in perhaps the best way the group could, they moved on with the important work of the WG.
Hervé Clément and Constanze Bürger gave an update from the NRO NC with a focus on progress around ICP-2. If you want to help determine the core principles in ICP-2, a document that essentially spells out the criteria for establishing new Internet registries, go fill in the questionnaire they shared!
Next, Angela Dall'Ara presented a policy update from the RIPE NCC before Marco Schmidt gave his update from the RIPE NCC's Registration Services team. Followed by more Marco! This time talking about personal ASNs in the RIPE Registry and casting a wider lens on ASN usage and visibility.
Finally, and very worthy of note, Leo Vegoda informed the room that the APWG will be seeking a third co-chair, with the intention of filling the role at RIPE 90 in Lisbon. Those of you who might wish to apply have six months to mull it over!
DNS WG
Meanwhile, people over in the sideroom were busy solving the world’s DNS problems. Willem Toorop mentioned the recent DNS-OARC meeting and invited people to attend Thursday’s BoF on DNS resolver recommendations. Vesna then let everyone know about the upcoming Stockholm DNS Hackathon, scheduled for March 2025.
Research presentations took centre stage as Raffaele Sommese showcased a project on quickly identifying new TLDs to help combat domain abuse, with a call for collaboration from ccTLD and gTLD operators. Tamás Csillag from PCH discussed DNSSEC improvements, while Yevheniya Nosyk shed light on the Extended DNS Errors (RFC8914) and its potential for spotting misconfigurations in open DNS resolvers.
Roy Arends from ICANN detailed a fascinating case on domain "magnitude," revealing a bug in Microsoft Teams that caused a sharp spike in queries for the reserved TLD “scloud.” Anand Buddhdev closed the session by updating us on RIPE NCC’s DNS services, including plans to retire the secondary DNS service on ns.ripe.net and calls for additional AuthDNS hosts to bolster redundancy.

Address Policy WG II
Tobias kicked off the session with an update on his update to the PI policy proposal aimed at reducing registry space fragmentation and enhancing flexibility for end users. His focus was on adjusting policy language to support user needs better, though there was a request for a more concise approach!
Jordi followed with a proposal to streamline IPv6 allocations for LIRs, noting that about half of IPv6 allocation extension requests were not approved, which suggested something needed to change on the policy front. His proposal allows for initial allocations of either a /32 or /28, including allowing extensions to /28 for existing holders. The question was raised whether the WG would get trapped into a loop of endlessly expanding into the adjacent reservations thoughtfully made by the RIPE NCC but this is (probably) the last time!
Remco then introduced his proposal to simplify the different flavours of IP addresses. His goal? To reduce the unintentional gatekeeping effect of having so many contradictory, ill-defined or outdated definitions. He suggested there were two potential directions they could go in: adopt something like his proposed policy change or else move towards a unified manual-based approach, as seen over in the ARIN region.
The session ended with an open mic for miscellaneous topics. Nick Hilliard questioned the relevance of the multihoming requirement for ASNs in the current landscape. He argued that the RIPE NCC’s role is to document activities rather than enforce restrictions, particularly now that the return of per-resource charges had taken care of the “garbage collection”.
Lee Howard noted that people were often confused about temporary resource transfers – many people thought this triggered the two-year holding period, or else didn’t know they had a maximum one-year limit. Expect a proposal in the near future!
IoT WG
The S in IoT is for… Soltobaev, Aziz Soltobaev, who highlighted the unique challenges of networking in difficult terrains with LoRaWAN, emphasising the need for resilient sensor communication. Michael Richardson dove into the details of onboarding IoT devices, covering standards and lifecycle management. Troy Martin rounded off the session with a breakdown of the 802.11ah WiFi standard, comparing it to other standards and discussing its suitability for IoT.
RIPE NCC Services WG
The regular meeting programming ended with everyone’s favourite WG (ed: any data on that?). Since the RIPE NCC’s 2025 Activity Plan and Budget is now published for your input, the presentations were focused on the organisation’s plans for the upcoming year.
Hans Petter Holen started with the plans for our Registry division; which is divided into the Registration Services, Members Services, and Registry Monitoring teams. RS will be looking into greater automation, improving the way they record registry data internally and reviewing processes. Member Services will be looking at improving their billing procedures (please consider paying on time!), and improving their verification checks. Registry monitoring plans to increase the number of ARCs and improve sanctions screening.
Felipe then shared the plans of our Technology division. Key plans of note: increased security for services like the LIR Portal, SSO and RIPE Database (part of a company-wide effort). Improving work processes and greater automation, modernising data storage and infrastructure (and saving on costs in the process), and improving the user experience services like the LIR Portal and RIPEstat. Comment from the floor: security’s all well and good, but some of us like sharing passwords. Hear hear!
Anyway, distributing IP addresses and running key Internet infrastructure is all well and good, but what about the really critical stuff like this meeting blog? Hisham covered this in his plans for Community and Engagement. He didn’t mention this blog by name, but you can tell it was front and centre in his mind. Anyway, here nothing drastically changes – the RIPE NCC will be continuing to run events, developing new training and other “learning experiences”, publishing research, building relationships with governments and regulators, and engaging in important consultations such as the UN Global Digital Compact and WSIS+20 review. More importantly, guys, his RIPE Meeting post on LinkedIn scored 31,954 likes (and climbing!), but of course you know he’s not one to get all caught up in that stuff.
Hans Petter wrapped up the session by sharing the plans from our Organisational Sustainability division - the fine people who keep the lights on and prevent the office and regulatory walls from caving in around us. Here the name of the game is keeping the RIPE NCC on an even keel and prepared for the years ahead – implementing new legislation and enhancing our legal framework, securing our finding and managing risks, and strengthening the organisation’s security profile.
And with that, day three was done. Some people left to have a drink or explore the city, though the masochists among us checked that we had our GM sticker on so we could do our part in contributing to the membership-led governance of the RIPE NCC at the General Meeting.
Day 2: Dude, Who Stole My Charter?
Day two of RIPE 89 saw us continue with plenary presentations followed by the first two Working Group sessions of this meeting and ending with a session on diversity and inclusion.

Starting the day off in our first Plenary, Daniel Otten from Osnabrück University gave a presentation on reducing power consumption of backbone networks, explaining how the importance of energy consumption management increased with the growth of the Internet and how more advanced Traffic Engineering techniques such as Segment Routing can help with the problem.
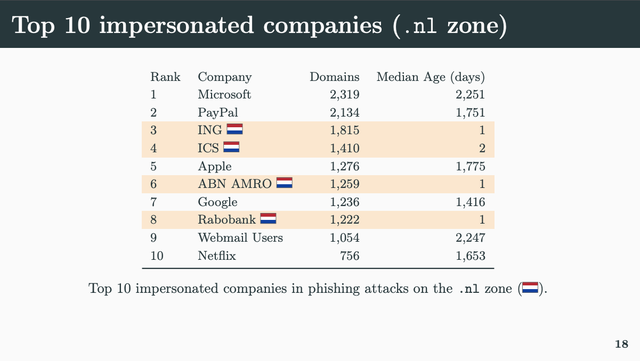
Next, Thomas Daniels of KU Leuven showed how phishing is seen from the vantage point of country-code Top Level Domains (.be, .ie, and .nl) and explored how it can be most effectively mitigated at different levels (at the registry, registrar and hosting provider).
Aniketh Girish from IMDEA Networks Institute then shared an investigation into smart home IoT devices communicating over the network and the potential threats due to these devices, particularly with the possibility of household fingerprinting, surveillance and cross-device tracking.
Break for coffee and then - boom - second plenary session! We started off with Igmar Poese from BENOCS looking at Ingress Point Detection (IDP) as a tool ISPs can use to improve their network operations by identifying performance issues and advancing traffic engineering practices. Remi Hendriks (University of Twente) then showcased a RACI research project that gathered insights into the current anycast landscape and supporting operators to improve traffic engineering decisions and the resilience assessment of third parties. Finally, Dmitry Belyavskiy from Red Hat introduced some standards being developed in the context of the post-quantum (PQ) transition, for example those replacing digital signatures. He also discussed the consequences PQ algorithms could have on network protocols.
After lunch, our third plenary began with a presentation from Jason Goertzen of Sandbox AQ and Peter Thomassen and Nils Wisiol of deSEC. They explained that as quantum computers develop, they pose a risk to current cryptographic standards, particularly in DNSSEC, which relies on public-key cryptography for secure domain name resolution. To address this, NIST has proposed three quantum-safe algorithms that could maintain security against quantum and classical threats.
Next, Anna Wilson of HEAnet taught us that successful automation isn’t just technical — it demands fundamental organisational adaptation and alignment. Understanding your organisation's “unit of currency” — the primary way they allocate resources — is crucial to navigating similar transformations.
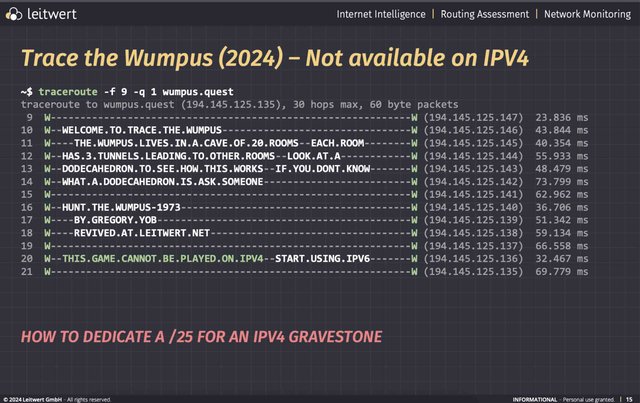
Johann Schlamp of Leitwert introduced us to “Trace the Wumpus,” an update of the interactive text adventure “Hunt the Wumpus” from 1973. Finally, a game for traceroute enthusiasts!
Next, Andrew McConachie of ICANN shared that the ICANN Board has permanently reserved the .INTERNAL domain as a private-use Top-Level Domain (TLD) in the DNS root zone, aiming to provide a standardised option for private network naming. The goal is for network administrators to adopt .INTERNAL for internal resources rather than using a mix of other TLDs. And wrapping up this plenary session, Ioannis Arakas of FORTH and UOC taught us how End-of-Life (EoL) software - i.e. versions no longer supported by vendors - can be easily exploited due to unpatched vulnerabilities. Alarmingly, over 9 million IP addresses run EoL software, and common EoL applications include Nginx, Apache, and PHP.
MAT WG
Over in MAT WG, Jim Cowie gave a brief overview of historical data held through RIPE Atlas and talked about how this should be preserved for generations to come.
Etienne Khan gave us a first look at user-installed residential proxies from a network operator’s perspective. Etienne shared his findings and key takeaways on what to watch out for concerning phishing and sophisticated bots.
Tianrui Hu presented his research on whether a smart home can be fully ready for IPv6. Conclusion? Not at the present moment. More discussions are needed on what device vendors, network providers, and all the good folks at this meeting can collectively do about this.
The IPv6 address space makes exhaustive scanning unfeasible, so researchers rely on hit lists of active addresses, often expanded by Target Generation Algorithms (TGAs). Lion Steger shared his research on whether these hit lists accurately represent the IPv6 Internet or if they introduce biases.
Vasilis Giotsas analysed the APNIC per AS user population dataset and found it effective in countries with enough Google Ads data. Checking the user-to-sample ratio improves accuracy, and understanding data nuances is crucial to prevent misinterpretation.
Finally, Emile Aben from the RIPE NCC presented "RPKI Flutter," a project to track real-time fluctuations in RPKI data and its impact on BGP routing. The tool captures frequent changes in RPKI data and reveals patterns unseen in BGP alone. Emile asked for feedback and engagement with the dataset to further analyse RPKI’s role in network stability.
Anti-abuse Security WG
The Security WG session started with an overview of its new charter. The Anti-Abuse WG is now the Security WG.
As dark regulatory clouds gather over yonder horizon, the RIPE NCC’s Hisham Ibrahim requested a dialog with WG participants on this topic, as governments in our region look to set various wrongs to rights. He will also be presenting on this in the Cooperation WG on Thursday.
Antonia Affinito from the University of Twente presented an analysis of the different domain blocklists used to protect against cyberthreats. The research covered four years and looked at the blocklists’ effectiveness and long-term consistency.
Lee Kent, BeIN, and Andrew Willatt from the Premier League presented on piracy on the Internet and their organisation’s attempts at contacting the users of IP addresses that are being used for the piracy. They requested some help from the community to figure out how to do this best, as they have had difficulty getting a response from network operators.
Day 1: Choose Wisely
RIPE 89 is the fourth time that a RIPE Meeting is being held in beautiful Prague, resplendent in its autumnal colours. You can watch the sessions, you can view the slides, but if you really want to know what’s happening, read our Daily Meeting Blog!
The 89th RIPE Meeting kicked off today. As RIPE Chair, Mirjam Kühne mentioned in her opening, the previous RIPE Meetings held here discussed allocations from the last /8, CIDR, and …IPv7! What will we end up discussing by this Friday?

Crash Courses
You learn a lot at RIPE Meetings, and there were three crash courses in the Opening Plenary - Ondřej Filip, the local host, welcomed attendees to RIPE 89 and explained the hierarchy of Czech holidays. The end of communism is celebrated by capitalism (Level 1 holiday) and today’s Czech National Day doesn’t mean that the end is nigh (pubs are open). The Programme Committee gave a one-slide overview of whether AI will help your talk get accepted for a RIPE Meeting plenary session (Spoiler alert: It won’t).

Fredy Kuenzler gave us a crash course in Swiss governance as part of his talk on what can go wrong with FTTH. Make notes - the ComCom and ComCo are two different entities! Fredy gave a presentation about the ‘Glasfaserstreit' (fibre optic dispute), an antitrust case,which prevented the monopolisation of the Swiss fibre optic network.

Geoff Huston presented remotely, an unfortunate (errr crash course in) firsthand experience of Newton’s first law of motion while riding a bike having prevented him from travelling to Prague. Geoff asked why there’s been so much resistance to the adoption of security measures like DNSSEC and RPKI in Internet infrastructure, despite nearly three decades of efforts.
Richard Patterson from Sky UK Ltd kicked off the second Plenary of the day with his presentation on IPv6-only with IPv4aaS (MAP-T). Richard led the attendees through the ins and outs of “IPv4-as-a-Service” (IPv4aaS) which led to a fruitful Q&A discussion upon its conclusion.
Benoit Claise from the IETF was up next with his presentation on the Next Era of Network Management Operations. Benoit, joined on stage by his IETF colleague Mirja Kühlewind engaged in an outreach effort regarding a workshop - organised by the IETF and IAB (Internet Architecture Board) with regards to an operation which began 22 years ago called RFC 3535, "Overview of the 2002 IAB Network Management Workshop", which collected requirements & recommendations, and which lead to some IETF developments. Following this there were 3 lightning talks presented by Andrew McConachie of ICANN on rssac002.root-servers.org, Mikhail Klimarev of the Internet Protection Society on Throttling YouTube in Russia: Impact on Telecom Infrastructure and Access to Information and August Bournique of the Law Office of August Bournique on The Cyber Resilience Act and Open Source Projects.
Day 1 wrapped up with the BCOP Task Force session with two talks. Since 2023, efforts have been made to document the practices of network operators in Ukraine in war and to set up a network operators group - NOGUA. NOGUA has made efforts to support network operators maintain resilient networks on the frontlines and successfully held its first meeting.
The other talk focused on the definition of “consensus” in RIPE. It’s clear when we agree to disagree, but it’s less clear when we agree to agree. Whether you agree with the need to document consensus or disagree with the definition of agreement - the BCOP TF wants to hear from you!
The session ended with everyone agreeing to agree that the Welcome Reception was the perfect way to end a very busy first day of RIPE 89! We couldn’t agree more…





Comments 1
Rob Evans •
“(ed: any data on that?)” Do you need to ask?