The Middle East’s Internet landscape is diverse and complex, with big variations between the GCC countries and areas such as the Levant and North Africa. Ahead of MENOG 24, we look at the development of Internet technologies in the Arabic-speaking countries of the region that have the potential to become major players in the global digital revolution.
The MENOG 24 meeting takes place on 4-5 December in Muscat, Oman. You can register for the event on MENOG website.
The Middle East and North African (MENA) region presents a complex and rapidly evolving Internet landscape. While Gulf Cooperation Council (GCC) countries are pushing forward with advanced infrastructure and initiatives, others face challenges in investment and connectivity. At the same time, regional collaboration, alternative routing strategies, and the influx of global tech giants are shaping the future of Internet connectivity in the region. This report provides an overview of key trends, challenges, and developments in the region's Internet infrastructure and connectivity.
RIPE NCC engagements with Middle East governments and operators
As the Regional Internet Registry (RIR) for Europe, the Middle East and parts of Central Asia, the RIPE NCC has a crucial role to play in supporting the development of a robust, secure and future-proof Internet infrastructure across our service region. This calls for ongoing engagement with policymakers, regulatory leaders, government representatives, and other telecommunications industry stakeholders who are well-positioned to drive the adoption of key technologies like RPKI and IPv6.
Our approach to engagement in the Middle East is built on a foundation of long-term, strategic collaboration with a diverse set of stakeholders. We understand that driving the adoption of new Internet technologies requires more than just technical expertise - it requires building trust, alignment and momentum among key decision-makers and influencers. That's why we invest heavily in developing strong relationships with governments, regulators, the ICT industry, academia and other influential players, and work closely with them to gain a clear understanding of their needs.
Through meetings and workshops with stakeholders, we conduct market and technical analyses to identify opportunities for adoption. Each such engagement provides us with a new opportunity to highlight the benefits and best practices for implementing Internet technologies and to learn more about the specific needs and constraints of each country. Tailoring our approach to the local context, we provide support that aligns with national digitisation agendas and delivers real value for the RIPE NCC's partners.
Our efforts have delivered concrete results in several countries across the region. In Saudi Arabia, for example, engagement with local operators and authorities has helped drive significant progress on RPKI adoption. Similarly, in the United Arab Emirates, the RIPE NCC's collaboration with key stakeholders has contributed to accelerating IPv6 deployment, ensuring that the country's networks are well-positioned to meet the demands of future growth and innovation. These results have been recognised. At the 27th meeting of the Council of Arab Information and Communications Technology last January, for instance, Ministers who convened in Abu Dhabi for the event applauded RIPE NCC efforts on this front.
In the rest of the article, we will discuss technology adoption in the light of these engagements.
The state of routing security in the Middle East
Routing security is fundamental to maintaining a stable and resilient Internet. As networks grow more complex, the risk of route hijacks and misconfigurations increases, and with it the potential for service disruptions and data interception.
RPKI provides a cryptographic framework for verifying routing announcements, currently through the use of two main key components:
- Route Origin Authorisation (ROA): A digitally signed object specifying which Autonomous Systems (ASes) can announce specific IP prefixes.
- Route Origin Validation (ROV): The process of using ROAs to verify routing announcements, classifying routes as Valid, Invalid, or Not Found. Invalid routes can then be dropped.
The evolution of routing security is demonstrated through major incidents.
In 2008, before RPKI, an accidental prefix hijack of YouTube-held IP addresses by Pakistan Telecom occurred that led to a global service outage and highlighting the Internet's vulnerability to routing incidents at the time.
In contrast, during Cloudflare's 1.1.1.1 service disruption in June 2024, ROV prevented widespread propagation of incorrect routes. Similarly, in July 2023, an attempt to block Telegram in Iraq remained localised as networks implementing ROV automatically rejected the invalid routes thanks to Telegram's ROA deployment. In both post-RPKI cases, the infrastructure effectively contained the impact of the misconfiguration/manipulation and prevented further damage.
Adoption of RPKI is increasingly recognised as crucial not only by network engineers but also at the government level. We previously reported that this year the US government advocated for the implementation of RPKI on federal networks as a way to address BGP vulnerabilities. Similarly in the Middle East, governments have been taking decisive action toward the adoption of RPKI and, as a result, we see many countries across the region achieving high ROA coverage.
BGP incidents
Before diving into the RPKI adoption data, we analysed BGP incidents in the region and neighbouring countries using Cloudflare's BGP incident data. Each incident is counted once per country, whether the country involved was hijacker or victim. An incident is defined by a unique combination of the incident ID and the ASNs involved (for both hijacker and victim ASNs).
For the period analysed, as we see below, Iraq had the highest number of incidents, followed by Jordan, Saudi Arabia, and the United Arab Emirates (UAE). Oman and Yemen saw only very few incidents, and Syria, none at all. (Note that incidents where country attribution was not possible for both parties were excluded from this analysis.)
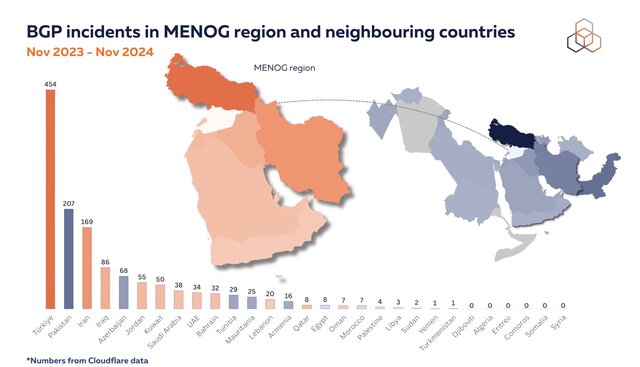
While analysing incident volumes provides a broad view of BGP routing health across countries, it's crucial to understand that even a single incident can have severe consequences. A BGP hijack targeting financial institutions could disrupt banking services and transactions, while one affecting government networks might compromise essential public services.
Similarly, hijacks of infrastructure-related prefixes (like those belonging to ISPs, DNS providers, or critical Internet exchange points) can cause widespread disruption for Internet connectivity and digital services. Therefore, while some countries show lower incident counts, the potential impact of any BGP incident makes route security measures like RPKI crucial for all networks, regardless of historical incident volumes.
RPKI adoption in the Middle East
As noted, the Middle East shows strong RPKI adoption, with ROA coverage ranging from 40% to nearly 100%. IPv4 ROA coverage consistently shows higher percentages across the region compared to IPv6, primarily because IPv4 address space is concentrated among larger providers, making implementation more centralised. In contrast, IPv6 space is often distributed across a broader range of ISPs or other Local Internet Registries (LIRs) which can lead to varying adoption rates.
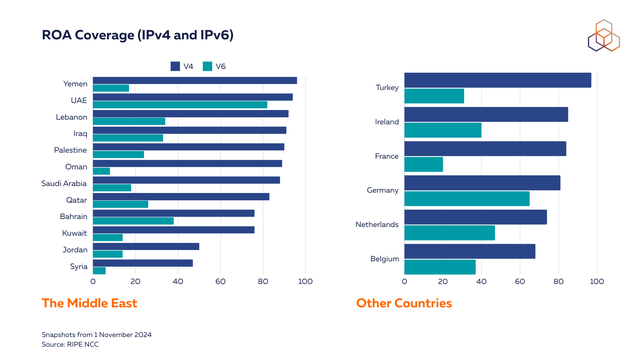
The United Arab Emirates stands out with exceptionally high ROA coverage across both IPv4 and IPv6 address spaces, indicating comprehensive implementation of RPKI across their network infrastructure. This dual protocol coverage suggests a systematic approach to routing security in the UAE's digital infrastructure.
A notable success story is Oman, where ROA coverage surged in 2020-2021. This significant increase was driven by two major operators - Omani Qatari Telecommunications Company and Omantel - creating ROAs for their IPv4 space. This coordinated effort by key infrastructure providers resulted in Oman achieving over 85% coverage, demonstrating how targeted adoption by major operators can rapidly improve a country's routing security posture.
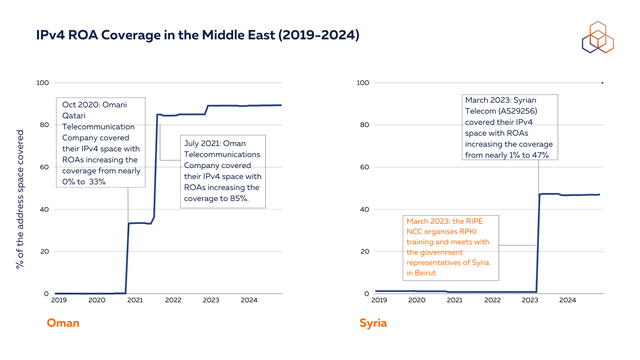
Providing training for operators is one of the most effective ways to strengthen digital resilience in a country. In the UAE, Saudi Arabia and Syria, for example, we conducted RPKI training (and also a follow-up webinar for the UAE) through 2023. The training was hosted by the UAE regulator and included participation from national operators, Du and Etisalat. Following the training, Etisalat covered their IPv4 space with ROAs, increasing their coverage to over 90%.
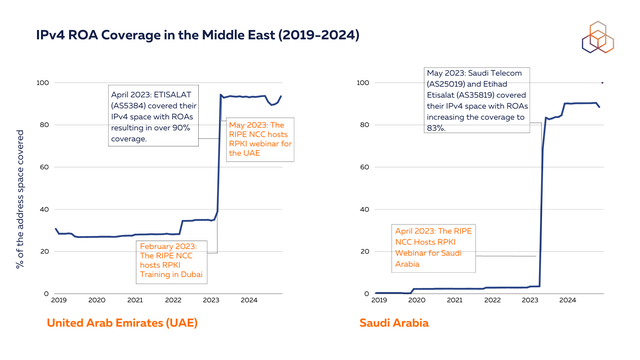
And again, we saw considerable increases in ROA coverage in Saudi Arabia and the UAE following engagements between the RIPE NCC, local operators and the governments of both countries.
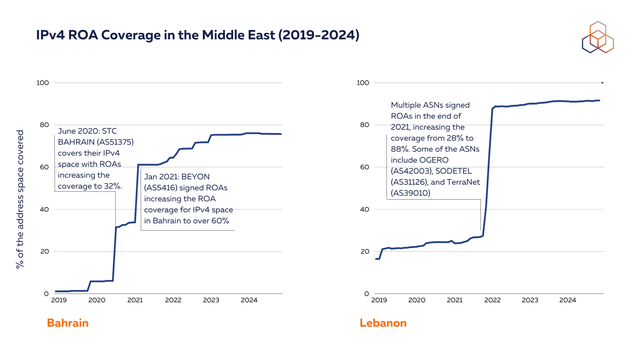
Bahrain and Lebanon are also showing high levels of ROA coverage with large operators signing ROAs for their IPv4 space.
ROV through the lens of network centrality
After creating ROAs, the crucial next step in RPKI-based routing security is ROV. ROV ensures that route announcements match the authorisations specified in ROAs. Using RoVISTA, which calculates scores based on an AS's ability to reach RPKI-invalid prefixes, we analysed ROV deployment across the region. The RoVISTA methodology relies on the IP-ID Side Channel, which enables remote clients to make educated guesses about a host's ability to send TCP packets to other hosts. This measurement approach requires vantage points inside an AS to gather data, which means our analysis may have gaps where such vantage points weren't available.
To understand the impact of ROV deployment, we examined network centrality using AS Hegemony methodology. This approach measures how essential each autonomous system is to a country's routing infrastructure. In our visualisations, the size of each AS representation corresponds to its routing centrality within the national network.
While our analysis shows promising ROV deployment results, the interpretation requires careful consideration. It's important to note that a ROV score doesn't conclusively indicate whether an AS has implemented ROV directly. An AS might show positive ROV filtering behaviour due to 'collateral benefit' - protection inherited from ROV deployment by its upstream providers. Conversely, when we identify networks that can reach invalid prefixes, it indicates that neither the network itself nor any of its upstream providers have implemented ROV, making these cases particularly important to highlight.
ROV deployment by highly central networks is particularly impactful for the broader routing security ecosystem. When major ASNs implement ROV, they not only protect their direct customers but also create a protective effect for smaller networks connected to them, helping prevent BGP origin hijacks. This makes ROV deployment by central ASes, particularly those providing significant transit services, especially crucial for enhancing regional routing security. In our AS visualisation, we specifically highlight central ASes that haven't deployed ROV, as they represent key opportunities for improving routing security.
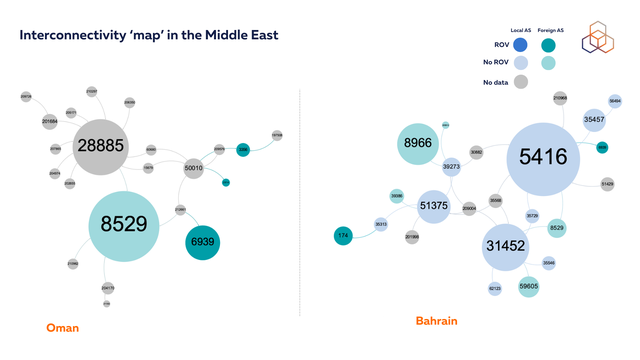
According to our analysis, most of the central ASes local to the Middle East don’t deploy ROV for their IPv4 space (in some cases no data is present). It is noteworthy that, in contrast to the findings from our analysis of Central Asia in September this year, the Middle East region exhibits a stronger regional interconnectivity, with several large foreign networks displaying high centrality.
This increased interconnectedness is beneficial for the resilience of the region's Internet infrastructure. For instance, in Bahrain, ASes registered in the United Arab Emirates - e.g. AS 8966 (Etisalat); AS 59605 and AS 8529 (both belonging to Zain Omantel) - have high hegemony scores. This indicates that these networks play a significant role in the country's internet connectivity and have a substantial influence on the flow of data traffic. The presence of these key regional players in Bahrain's network landscape highlights the importance of fostering strong regional ties and collaborations to enhance the stability and performance of the Internet infrastructure in the Middle East.
In Oman, our RoVISTA analysis reveals a data gap for the major telecommunications provider, Omantel (AS28885), as we lack the necessary vantage points for measurement. Of particular interest is Zain Omantel (AS8529), which appears as a foreign network in our visualisation due to its registration details. This classification stems from a recent joint venture between Zain Group and Omantel called Zain Omantel International (ZOI), which manages wholesale services across eight countries serving over 55 million customers.
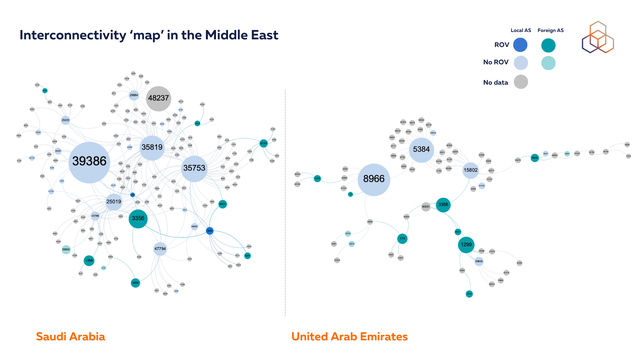
We are currently collaborating with operators in UAE and Saudi Arabia on deploying ROV and are at the testing phase.
Jordan's interconnectivity landscape shows promise for secure routing. Central ASes with high AS Hegemony scores - such as Jordan Telecommunications (AS8697), Jordan Data Communications Company (AS8376), and VTEL (AS50670) - have implemented ROV. However, other networks with significant routing centrality, including Jordanian mobile phone services (AS48832) and Batelco (AS9038), have not yet deployed ROV. Implementation by these central ASes would create substantial collateral benefits, enhancing routing security for their downstream networks and protecting against route origin validation failures, whether from malicious prefix origin hijacks or accidental misconfigurations.
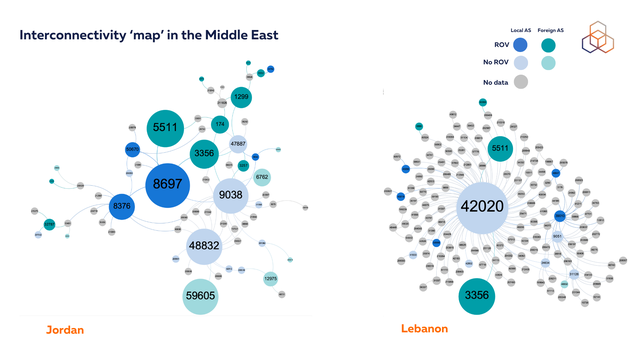
Lebanon presents an interesting case in routing security dynamics. OGERO/LibanTelecom maintains two significant ASes: AS42020, which shows high AS Hegemony scores, and AS42003, which serves the majority of the customer population according to APNIC data. While AS42003 has implemented ROV, protecting its substantial user base from invalid routes, AS42020 has not yet deployed ROV.
AS42020's position is particularly significant, representing nearly 100 ASNs and thousands of advertised networks from across the Lebanese economy. This makes ROV deployment crucial, as it would provide comprehensive protection against invalid routes across Lebanon's routing infrastructure and protect the substantial portion of the economy that relies on this network.
This case illustrates the multi-faceted nature of routing security. AS42003's ROV deployment effectively protects its large customer base. However, AS42020's central position in routing paths means its ROV deployment would create broader collateral benefits, protecting all networks that use it as an upstream provider. While having ROV on either AS improves routing security, implementing it on both would provide comprehensive protection against origin validation failures and misconfigurations across Lebanon's routing infrastructure.
Accelerating IPv6 deployment
IPv6 deployment remains a critical priority for sustained Internet growth, especially as IPv4 address space exhaustion continues to challenge network expansion. Beyond addressing scarcity, IPv6 offers opportunities for improved end-to-end connectivity, simplified network management, and enhanced security features.
Our analysis examines two key aspects of IPv6 progress in the region: routing capability and actual adoption. The capability metric measures infrastructure readiness, defined as the percentage of ASes in each country that announce at least one IPv6 prefix visible in the global routing table. While this indicates routing readiness, it doesn't necessarily reflect actual IPv6 traffic or user adoption.
To understand real IPv6 usage, we examined Content Delivery Network (CDN) data showing the percentage of users accessing content over IPv6. This metric provides insight into actual end-user IPv6 adoption, revealing how much IPv6-capable infrastructure is being actively utilised. The comparison between capability and CDN-based adoption metrics helps identify gaps between infrastructure readiness and practical implementation, highlighting where additional effort might be needed to drive IPv6 utilisation.
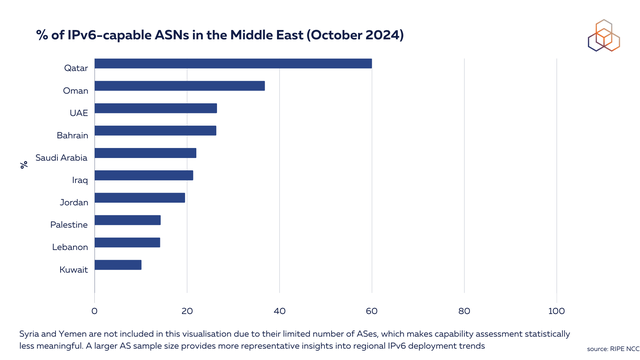
We looked into the capability and adoption of IPv6 in the region. On average, the percentage of IPv6-capable ASNs (defined here as the percentage of ASNs routing at least one IPv6 prefix) is 25% in the region with Qatar standing out (60%).
It is important to note that Syria and Yemen are not included in this visualisation below due to their limited number of ASes, which makes capability assessment statistically less meaningful. A larger AS sample size provides more representative insights into regional IPv6 deployment trends.
IPv6 capability only measures whether allocated IPv6 prefixes are actively announced in global routing tables. To assess actual IPv6 traffic patterns we analysed data from major CDNs, which provides insights into the percentage of users accessing content over IPv6. This end-user adoption metric complements our capability analysis by showing how much IPv6-enabled infrastructure is actively utilised.
According to CDN data, IPv6 adoption varies significantly across the Middle East, with some countries showing a notable disparity between their IPv6 routing capability and actual traffic volumes. This gap between infrastructure readiness and user adoption highlights areas where additional focus on IPv6 service enablement and end-user transition might be beneficial
Our analysis reveals interesting patterns between IPv6 capability and adoption in the Middle East. While Qatar leads in IPv6 capability (60%) followed by Oman (37%), UAE and Bahrain (26%), and Saudi Arabia (22%), the CDN traffic data tells a different story about actual IPv6 usage.
Saudi Arabia emerges as a regional and global leader in IPv6 adoption, ranking in the global Top 20 with over 50% of users accessing content via IPv6. While the IPv6 routing capability metric (22%) represents the percentage of networks announcing IPv6 prefixes, the higher adoption rate reflects actual end-user IPv6 traffic observed by CDNs. This difference highlights that while fewer networks might be announcing IPv6 prefixes, those that do - particularly large ISPs - are effectively enabling IPv6 for a significant portion of the country's Internet users.
The United Arab Emirates follows with over 40% IPv6 adoption, demonstrating successful translation of their routing capability into actual usage. Qatar, Oman, and Kuwait show promising adoption levels of 25-30%, suggesting steady progress in converting IPv6 capability into real-world implementation.
This comparison between capability and actual adoption metrics reveals that some countries have been particularly effective at enabling IPv6 services and driving user adoption, even with relatively lower IPv6 routing capability scores. This suggests that successful IPv6 deployment depends not only on infrastructure readiness but also on effective implementation strategies and service enablement.
| Country | IPv6 adoption (Google) | IPv6 adoption (Facebook) |
IPv6 adoption (Cloudflare) |
|---|---|---|---|
|
Saudi Arabia |
62% | 54% | 54% |
| UAE | 45% | 43% | 38% |
| Kuwait | 29% | 27% | 23% |
| Qatar | 28% | 31% | 31% |
| Oman | 24% | 24% | 28% |
| Bahrain | 17% | 15% | 19% |
| Jordan | 13% | 16% | 15% |
| Yemen | 7% | 1% | 2% |
| Lebanon | 1% | 0.3% | 1% |
| Iraq | 0.6% | 0.6% | 3% |
| Syria | 0% | 0.3% | 0.5% |
| Palestine | 0% | 0% | 0.5% |
Conclusion
The Middle East's Internet landscape is undergoing a significant transformation, with notable progress in routing security and IPv6 adoption. The RIPE NCC's targeted engagements with governments and operators have played a crucial role in driving this change, as evidenced by the high levels of ROA coverage and the growing IPv6 adoption rates in several countries.
However, challenges remain, particularly in countries where ROV deployment is limited, and IPv6 adoption lags behind infrastructure readiness. Addressing these issues will require continued collaboration between the RIPE NCC, governments, regulators and operators to promote best practices, share knowledge, and implement effective strategies for improving Internet security and resilience.
As the region continues to embrace digital transformation, investing in secure and future-proof Internet infrastructure will be essential for unlocking the full potential of the digital economy and ensuring that the benefits of connectivity are accessible to all. The RIPE NCC remains committed to supporting this journey through its ongoing engagement efforts and technical expertise, working together with stakeholders across the region to build a stronger, more secure, and more inclusive Internet for the Middle East.
By attending events like the upcoming MENOG meeting in Oman, network operators, policymakers, and other stakeholders can gain valuable insights, share experiences, and collaborate on solutions to drive the continued development of the Internet in the Middle East. As the region navigates the challenges and opportunities of the digital age, a strong and resilient Internet infrastructure will be the foundation for growth, innovation, and prosperity.
You can still register for the upcoming MENOG meeting that will take place on 4-5 December in Oman. Prior to the plenary sessions, the RIPE NCC and partner organisations we will host trainings and workshops on IPv6, routing security, and peering. You can register for the events on MENOG website.







Comments 3
Milad Afshari •
It was really helpful; thanks for sharing this information. While Iran and Turkey were mentioned in the Routing Incidents statistics, it would have been even better to see insights and data on these countries in other areas, such as ROA, ROV, and IPv6 adoption. Considering that Iran and Turkey are significant parts of the Middle East, including these details would provide a more comprehensive view of the region’s Internet landscape...
Hide replies
Anastasiya Pak •
Hi Milad, thank you for the comment. As we had already focused on Iran as part of our earlier analysis ahead of CAPIF 3 (you'll find the link in the 'related articles' section above), this time we decided to focus our attention on the Arabic-speaking countries of the region. We apologise for not making this clearer in the article. The good news is that we'll be producing more of these reports and we'll definitely take your feedback into consideration!
Arash •
Great insights on the Middle East's Internet progress! However, I couldn’t help but notice Iran’s absence from the report. Did it somehow get misplaced on the map? Perhaps it’s time for a quick geography refresher. I hear geography lessons can be just as engaging as IPv6 workshops—maybe even more so with the right trainer!