The Domain Name Service Look-aside Validation Service (DLV) was an idea which was useful in the transition from a non-signed DNSSEC root to the current globally visible DNSSEC trust anchor. Now a significant number of people in the wider Internet may be running (particularly) Linux distributions that out-of-the-box expect the DLV service to be running, and provide valid answers.
At RIPE 70 in Amsterdam, Jim Martin (Internet Systems Consortium) presented on the end-of-life issues of DLV .
DLV, or the Domain Name Service (DNS) Look-aside Validation Service , was an idea which was useful in the transition from a non-signed DNSSEC root to the current globally visible DNSSEC trust anchor: Some people wanted very badly to be able to DNSSEC sign and test before their specific parent domain under the root was DNSSEC enabled, to practice risk management and to ‘blaze the train’ in DNSSEC. So, ISC decided to run a DLV, so they could configure their resolvers (the DNS request side servers) to look at the DLV service before looking in the root, to find the DNSSEC security information over the name (which in the real DNS system didn’t have a DNSSEC enabled parent. The rule is you can only do DNSSEC when your parent does, all the way back to the root).
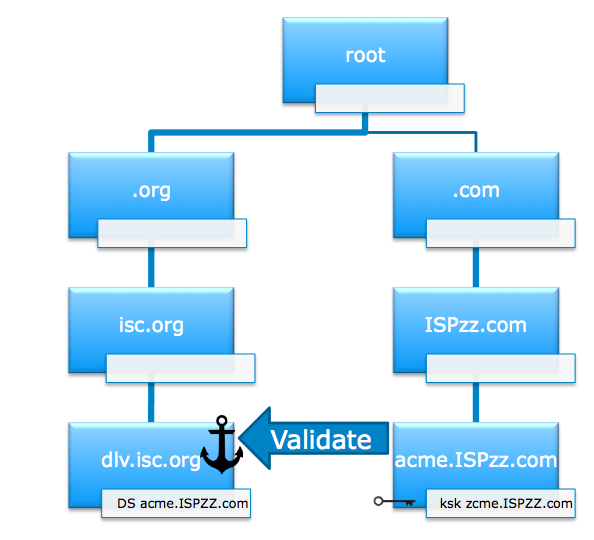
DLV was useful for some people. And ISC, (who manage and code the “bind” DNS code, which is almost ubiquitously distributed worldwide in UNIX systems) decided to make it work in their code by default but leave it turned off, however the inevitable has happened.
If you make something sometimes work on the Internet, somebody somewhere else will make it happen always without asking you first.
We now have a situation where a significant number of people in the wider Internet may be running (particularly) Linux distributions that out-of-the-box expect the DLV service to be running, and provide valid answers.
So, what’s the problem?
The problem is, if the DLV is turned off, these services don’t “fail soft” by returning to the normal DNSSEC tree and the normal root. Well, to be fair, they partially do: For DNSSEC signed data, they will find the real DNSSEC signed root. All is good.
But for all the unsigned names in the global DNS, they will return the magic “SERVFAIL” signal and the names will not be looked up properly. That means the (majority) of the unsigned DNS, will be invalid, for all the people who run code that expects the DLV to operate.
Jim is leading a public review process to refine the timeline to wean the world off this risk. About 4,500 domains who are validly signed in the real DNS can be removed cleanly. Another 350-odd domains are ‘orphan’ under the DNS because their parent zone is not signed. He’s looking into what can be done to resolve them by 2016/17. On the resolver side, the community needs to update code to remove dependencies on the DLV, so that by 2017 (in the light of experience it might be sooner) the service can be disabled with the minimum of disruptive risk.
This is an interesting instance of the ethical dilemma highlighted by the Oxford Internet Institute : Deploying services without understanding the long term public-interest consequences, is a form of experiment on the public which isn’t well understood for its ethical risks. DLV was a good idea, but perhaps in hindsight…
Note that this was originally published on the APNIC blog .



Comments 0
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.