Serial hijackers are malicious actors that repeatedly carry out prefix hijacks on various networks, some lasting for months or years. A new study assesses the evolution of serial hijacking events since 2019 and determines what actions the technical community is taking to protect the Internet against them.
Despite its importance for the Internet's scalability and resilience, BGP remains vulnerable to prefix hijacks, which can disrupt access to critical services. While many prefix hijacking incidents are attributed to misconfigurations, we argue that they should not be dismissed lightly. Even accidental BGP hijacks can lead to significant security breaches and service outages.
In this article, we want to shed light on this issue and highlight the importance of proactively addressing these risks by creating Route Origin Authorizations (ROAs) for both used and unused prefixes and enforcing Route Origin Validation (ROV) to mitigate the impact of such events. The following is a summary of a paper we recently presented.
BGP: Security vulnerabilities and current countermeasures
The Border Gateway Protocol (BGP) is the Internet's most crucial protocol for enabling networks, so-called Autonomous Systems (ASes), to share reachability information for optimal path selection and traffic routing. Additionally, it enables ASes to exchange routes without centralised control, giving the network operators flexibility of originating prefixes (range of IP addresses) to their upstreams, peers and other networks without any default authentication mechanism to validate the ownership of network resources.
Although this decentralised approach has enabled the growth and effective functioning of the Internet, it also poses a significant threat to the Internet infrastructure because of its vulnerability to prefix hijacks and other problems.
Prefix hijacks and countermeasures
BGP's lack of a default mechanism for connected ASes to verify the authenticity of available routes is commonly exploited to cause wide-scale malicious or unintentional hijacks of network prefixes, compromising access to critical systems and services.
For instance, the recent hijacking and route leak incident involving a more specific prefix (1.1.1.1/32) of Cloudflare's 1.1.1.1 made the DNS resolver unreachable for about 300 networks in 70 countries for 7 hours and 37 minutes before it was fully resolved.
BGP extensions such as ROV can partially prevent prefix hijacks, but they have yet to achieve broader coverage. Other measures like ASPA and BGPSec are either in their early deployment stage or have yet to be deployed in the wild.
Motivation for studying BGP serial hijackers
Testart et al. coined the term "serial hijackers" to refer to malicious actors that repeatedly carry out prefix hijacks on various networks, some lasting for months or years. Subsequently, they used multiple datasets to transform the characteristics of serial hijackers into statistical features to profile serial hijackers in the wild.
However, these authors remain the only ones who have studied serial hijacking events since 2019, relying on terabytes of BGP data, which is a challenge for researchers with limited resources. Therefore, the motivation for our research is to (i) validate their method using less data, (ii) assess the evolution of serial hijacking events since 2019, and (iii) determine the actions taken by the Internet community in response to the reported alleged serial hijackers.
Our approach
We selected only a 5-minute daily snapshot of the "peer-pfx-origins" dataset for 2014-2018 and used CAIDA's BGPView tool to compute the recent snapshots for 2019-2023. We augmented the above data with RIR delegation files and longitudinal Multiple Origin ASes (MOAS) datasets, consisting of prefixes that originated from more than 1 AS. Finally, we used the above datasets to study the dominant attributes of serial hijackers with our sparse datasets and transform them into statistical features for our classification.
Findings: 1. Classification of networks with sparse data
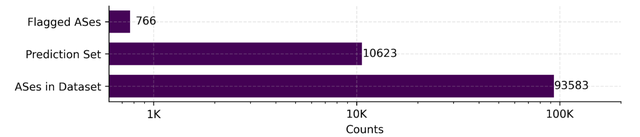
We relied on computed features from our sparse dataset for the ground truth (240 ASes) and the prediction set (10,623 ASes originating at least 10 prefixes) to train and evaluate our machine learning classifier to assess the current dynamics of hijacking events.
Of the 240-ground truth ASes, 23 were malicious networks reported in the NANOG mailing list for repeatedly hijacking prefixes, and the remaining 217 were benign networks. Our results show that it is sufficient to characterise the long-term attributes of regular and malicious networks with our sparse dataset, validating the redundancy in the dataset.
Our model subsequently flagged 766 ASes out of our prediction set (10.6K), as shown in Figure 1. We first compared our flagged ASes with those identified by Testart et al. in 2019. We found that both models flagged 279 ASes (36.41% of our flagged networks) as having the characteristics of a serial hijacker, confirming a reasonable agreement between both models on the existence of serial hijackers.
In summary, we observed indications of potential malicious and legitimate unconventional behaviour among our flagged ASes. For example, our flagged ASes were more likely to be found within the blacklisted ASes than unflagged ASes.
Finally, we also found that alleged serial hijackers often remain active or at least allocated by the regional Internet registries.
Findings: 2. The fate of the alleged serial hijackers
We used RIPE RIS data and archives of IP address allocations and assignments of the 5 RIRs to determine what happened to the 23 alleged serial hijacking ASes from 2019.
We found that 9 ASes (39.0%) were still active by the end of 2022 and announcing prefixes. 8 ASes (34.8%) were not allocated for some period after their hijacking activities but were later reallocated by RIRs at some point. It is unclear if the new owners were different from the previous ones.
Finally, 4 ASes (17.4%) are not allocated or reallocated anymore, and 2 ASes (8.7%) were still allocated to the same entity but not announcing any prefixes visible in RIS.
Additionally, the time it takes until a serial hijacking AS is de-allocated varies. For instance, ASes remained assigned for a median of 239 days after the last BGP announcements, while 2 ASes continued to announce prefixes for 20 to 24 days when they were not allocated, and we considered the announcements in question to be invalid.
In summary, 60% of the alleged hijackers were no longer active. However, whether the ASes in question became nonactive voluntarily or due to actions like de-peering or de-allocation is unclear. About 40% of the alleged hijackers were more active on the global routing table by the end of the study period than they had been before. One possible explanation could be that their irregular behaviour was due to mismanagement, which was later resolved. Another explanation could be that the community did not punish them for their malicious behaviour.
Discussion: Validating intentional hijacking
Although we have identified suspicious behaviour among our flagged ASes, it is challenging to ascertain the intent of prefix hijacking, due to the complex implicit relationships among ASes.
For instance, we studied the behaviour of an alleged serial hijacker (AS19529) in detail. 41.6% of its announced prefixes belong to AS20473, AS397460 and AS39879. Further investigation showed a customer-provider relationship between AS19529 and AS397460, which is technically possible as claimed but is not a recommended practice. As a result, we recommend further studies to determine the impact of legitimate MOAS prefix origination and IP leasing on hijacking classification systems.
Responding to hijacking and immediate actionable recommendations
Even if we could reliably identify potential serial hijackers, the research and operator communities still need to decide how to deal with them. Therefore, a carefully crafted approach of “naming and shaming” could positively impact the security posture of the interdomain routing ecosystem, thereby promoting transparency and accountability.
Similarly, RIRs such as RIPE NCC could initiate and lead a collaborative effort among academic researchers, the industry, legal practitioners and all stakeholders involved in the Internet's governance to develop a standard and robust reputation system to classify ASes based on their prefix origination behaviour, and make their reputation scores public to minimise potential malicious hijacks.
Like the MANRS initiative, we also believe an increased adoption of RPKI's ROA and enforcing ROV would significantly mitigate most of the origin hijacks we observed among the alleged serial hijackers. Therefore, we stress the importance of a collaborative effort among network operators to register ROAs for all their prefixes, including the unused ones, and enforce route validation. A united front of that kind would facilitate development of a more resilient and secure interdomain routing ecosystem.
Limitations and future work
Our single daily snapshot sampling method is prone to missing short-lived hijacks, plus it will not detect malicious actors carrying out path hijacks. Our classifier also recorded false positives, such as flagging ASes originating a significant share of MOAS prefixes. Finally, our remaining flagged ASes still need to be validated. Therefore, we intend to provide a pipeline to infer the intent of prefix hijacking among the remaining unvalidated flagged ASes, and to use word embeddings like Word2Vec to extract crucial semantic features to reduce our false positives.
Conclusion
In conclusion, we have shown that it is possible to characterise networks with 99.6% less data than previous work, and we have developed a competing classifier that evaluates the current trends of serial hijacking activities. We observed potential malicious and legitimate peculiar behaviour among our flagged ASes, with some still involved in listed malicious activities.
Although we have not observed any increase in serial hijacking activities during the last 5 years (2019-2024), potentially malicious ASes still threaten Internet security. Finally, we have also confirmed that most of the alleged serial hijackers are still active on the Internet, indicating either that the routing community is still looking for a common approach to deal with malicious behaviour, or that the irregular behaviour of the ASes in question was due to mismanagement, which has since been resolved.
To learn more about our study, we encourage you to read our paper and contact us if you have questions or suggestions.
Acknowledgments
We would like to express our gratitude to the Network Security programme of the Twente University Centre for Cybersecurity Research (TUCCR) under grant number 20003215. Cristian Hesselman's work was also part of the CATRIN and UPIN projects, both of which received funding from the Dutch Research Council (NWO).



Comments 1
Ngange Jeng •
Job well done Mr. Jaw determination is the key to success and I know you can do it. This is very useful especially to those doing computer science and related fields.